Organizations that work with the U.S. government must adhere to strict procedures covering procurement protocols, nondiscrimination policies, and rigorous cybersecurity. That’s because working with government agencies often involves handling sensitive and legally protected data, and failure to comply can result in financial and legal consequences.
To effectively approach government contracting compliance, you must be prepared to align with stringent standards such as the Federal Acquisition Regulation (FAR) and the Defense Federal Acquisition Regulation Supplement (DFARS), FedRAMP, and the requirements outlined in NIST 800-171 (which forms the foundation of CMMC).
In this article, Vanta breaks down notable regulations and frameworks for government contractors and the challenges you may face while pursuing them.
Organizations that work with the U.S. government must meet strict quality and security standards, and compliance frameworks are an effective way to standardize those requirements. These regulatory frameworks apply to organizations across a wide range of industries, including defense contractors, cloud service providers (CSPs), and other entities that process or store government data.
Adhering to government standards positions your organization as a credible partner, bringing in benefits such as:
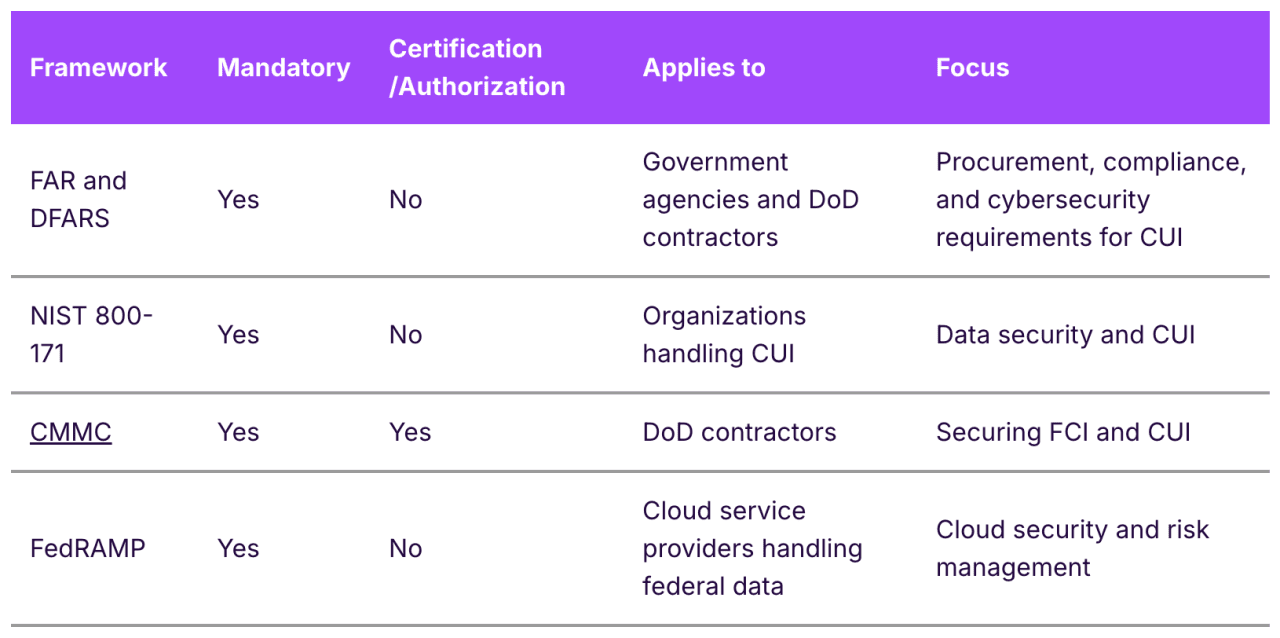
The FAR is a regulation introduced on April 1, 1984, with the intention of providing federal agencies with clear policies and procedures that establish a standard for purchasing supplies and services. Compliance with FAR is mandatory for both government agencies and organizations they contract.
The DFARS extends FAR for Department of Defense (DoD) contracts. DFARS introduces additional security and reporting requirements, particularly around handling Controlled Unclassified Information (CUI).
That means, if your contract involves handling CUI, you must comply with DFARS—which incorporates NIST 800-171 and now requires alignment with CMMC, the DoD’s certification framework built on NIST 800-171—to ensure your data security practices meet DoD criteria. Proposed updates to FAR also aim to make NIST SP 800-171 compliance a core obligation across federal contracting by standardizing how CUI requirements are identified and scoped.
To meet FAR and DFARS requirements, you need to implement a code of conduct, establish reporting protocols, and conduct regular training to ensure your employees understand and adhere to the rules.
NIST 800-171 is a special publication that provides organizations with controls for efficiently handling and securing CUI. Any organization intending to work with the U.S. government and process CUI must achieve compliance with NIST.
Compliance can be useful even for organizations that don’t intend to handle CUI since NIST can strengthen their security posture with stringent requirements across 17 families (as of rev 3):
Achieving compliance with NIST 800-171 doesn’t require a formal audit, and it doesn’t offer a certificate. You provide evidence of compliance to potential partners, who then determine whether your measures are sufficient.
Note: CMMC is built directly on the security controls in NIST SP 800-171, so many of the requirements overlap. However, CMMC adds formal certification and maturity levels, which is why we’ll discuss it separately below.
CMMC is a government framework developed by the DoD, sometimes also referred to as the Department of War under recent executive authority. Its purpose is to enhance the security posture of the Defense Industrial Base (DIB) and ensure the security of Federal Contract Information (FCI) and CUI.
Any organization that wants to work with the DoD must obtain a CMMC certification. The framework outlines requirements across 14 control domains, which incorporate practices from other frameworks such as NIST 800-172 and NIST 800-171 Rev 2.
The DOD recognizes that contractors and subcontractors handle different types of information, so the CMMC is structured into three certification levels, based on the complexity and sensitivity of the data you handle:
All three levels require annual affirmations to maintain compliance, while Levels 2 and 3 require a full reassessment every three years to maintain certification.
FedRAMP is a risk management program that standardizes risk assessments, authorizations, and continuous monitoring practices for cloud services working with government agencies. Compliance isn’t legally mandatory for all organizations, but it's a hard requirement for CSPs serving federal agencies. CSPs must obtain FedRAMP authorization before they can offer services to the U.S. federal government.
FedRAMP’s voluntary nature also means that you won’t receive penalties for noncompliance. However, failing to align with the framework may drastically limit business opportunities in regulated markets, even causing you to lose out on existing federal contracts.
The compliance process typically involves these steps:
The government sector framework you should pursue depends on the industry best practices and your current security posture. If you’re a cloud provider, you’ll need to comply with FedRAMP, which is built on NIST security controls. If you plan to collaborate with the DoD, you’ll need to meet CMMC requirements, which formalize NIST 800-171 controls for defense contractors.
The risks of noncompliance are high. Aside from financial penalties, noncompliance can lead to contract termination, loss of eligibility for future awards, and reputational damage.
If you intend to pursue government contracts but are still maturing your security posture, start by aligning with NIST CSF and NIST 800-171. Both frameworks provide strong security baselines that public sector buyers expect.
A major benefit of government compliance is that these standards are complementary and often share several controls. Once you achieve compliance with one of them, it'll be faster to meet the other.
Government compliance can be a complex and challenging process. Some of the most common roadblocks organizations encounter include:
Documentation expectations: Thorough documentation is nonnegotiable for government contracting compliance, but gathering the required evidence often involves sifting through disparate systems and siloed technologies, which puts significant pressure on your security and compliance teams.
A common mistake organizations make when pursuing government compliance is improperly scoping the environment or services they are providing as part of the contracts, leading to issues and delays in compliance programs overall.”
An effective way to approach this issue is to implement a top rated compliance automation solution that will enable real-time insights, centralize documentation, and ensure a consistent audit process.
Government contracting compliance is complex, but it’s also achievable with the right foundation. Frameworks like FAR, DFARS, NIST 800-171, CMMC, and FedRAMP are designed to protect sensitive data, and because they share common controls, progress in one area accelerates readiness in others. By taking a structured, continuous approach to compliance and leveraging automation to reduce manual effort, organizations can pursue federal contracts with greater confidence and less operational strain.
This story was produced by Vanta and reviewed and distributed by Stacker.
Reader Comments(0)